Scoped Permissions
Scopes let you specify exactly what type of access a token or user can have on Hathora. All tokens are scoped to a team. A user can only create a token with the permissions they have (i.e. viewer can only create read tokens).
Scopes
| Scope name | Description | Endpoints |
|---|---|---|
| billing:read-write | Read and update payment method. | GetBalance, GetUpcomingInvoiceItems, GetUpcomingInvoiceTotal, GetInvoices, GetPaymentMethod, InitStripeCustomerPortalUrl |
| builds:read | Read build metadata. | GetBuilds, GetBuild |
| builds:read-write | View, create, and delete builds. | GetBuilds, GetBuild, CreateBuild, RunBuild, DeleteBuild |
| deployments:read | Read deployment metadata. | GetDeployments, GetLatestDeployment, GetDeployment |
| deployments:read-write | View, create, and delete deployments. | GetDeployments, GetLatestDeployment, GetDeployment, CreateDeployment |
| applications:read builds:read deployments:read | Read application metadata. | GetApps (with deployment and build), GetApp (with deployment and build) |
| applications:read-write | View, create and delete applications. | CreateApp, UpdateApp, DeleteApp |
| processes:read | Read process metadata. | GetLatestProcesses, GetProcessesCountExperimental, GetProcess, GetRoomInfo, GetActiveRoomsForProcess, GetInactiveRoomsForProcess, GetConnectionInfo, GetMetrics, GetProcessesMetrics, GetLogsForProcess, DownloadLogsForProcess |
| processes:read-write | View, create and stop processes. | GetLatestProcesses, GetProcessesCountExperimental, GetProcess, CreateProcess, StopProcess, GetRoomInfo, GetActiveRoomsForProcess, GetInactiveRoomsForProcess, GetConnectionInfo, GetMetrics, GetProcessesMetrics, GetLogsForProcess, DownloadLogsForProcess, CreateRoom, DestroyRoom, UpdateRoomConfig, SetLobbyState |
| fleets:read | Read fleet metadata. | GetFleets, GetFleetRegion, GetFleetMetrics |
| fleets:read-write | View and update fleets. | GetFleets, GetFleetRegion, GetFleetMetrics, UpdateFleetRegion |
| orgs:read | Read orgs metadata. | GetOrgs, GetUserPendingInvites, GetOrgMembers, GetOrgPendingInvites |
| orgs:read-write | Add and remove users. | GetOrgs, GetUserPendingInvites, GetOrgMembers, GetOrgPendingInvites, InviteUser, RescindInvite, RejectInvite |
| tokens:read | Read token metadata. | GetOrgTokens |
| tokens:read-write | Create and view tokens. | GetOrgTokens, CreateOrgToken, RevokeOrgToken |
Scoped Tokens
You can use scoped tokens to limit system access to your game servers (i.e. matchmaker, CI/CD). Scopes for a token can be set when creating a token but can not be updated.
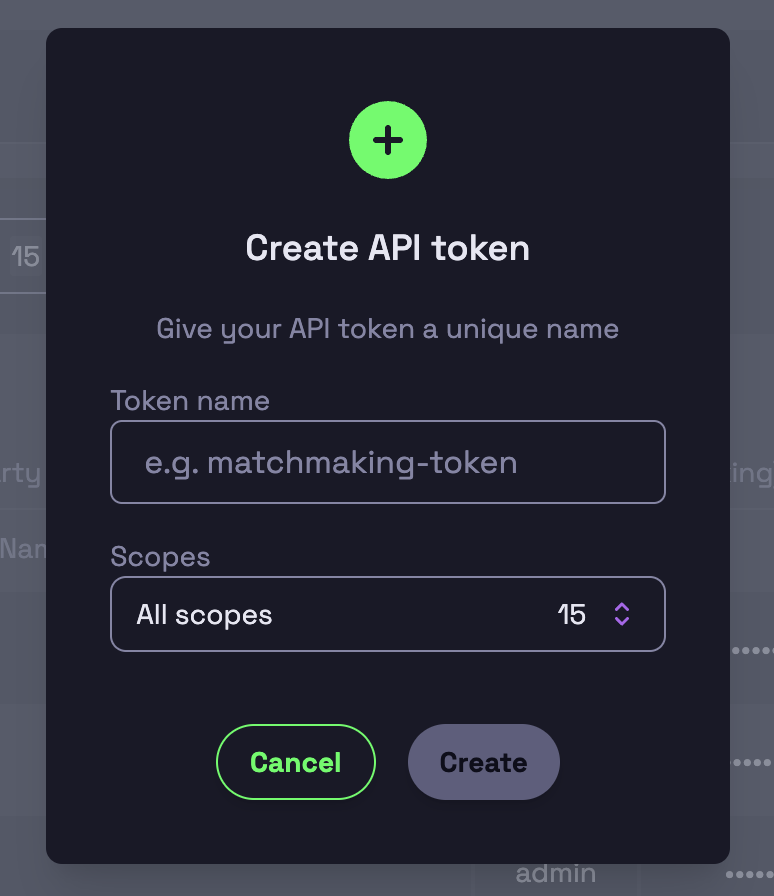
Scoped Users
Currently, a user can be an Admin, Member, or Viewer.
Admin
An Admin has full access to the entire Console. They can:
- Add and remove team members
- Update and view billing info
- Can make changes that can impact production processes
Member
A Member (i.e. engineer) is similar to an Admin, however they:
- Cannot add and remove team members
- Cannot view billing info
- Can make changes that can impact production processes
Viewer
A Viewer (i.e. QA team) has read-only access to the entire console expect billing. They:
- Cannot add and remove team members
- Cannot view billing info
- Cannot make changes that can impact production processes
- Can view process metrics and logs