Security
Hathora’s architecture integrates multi-layered security controls to provide protection against potential threats. This page describes some of these controls.
For questions, concerns, or information about our security policies—or to disclose a security vulnerability—contact us at security@hathora.dev.
Workload security
Workload security applies to Hathora single-tenant Pro and Enterprise customers.
Hathora guarantees complete compute isolation, ensuring your containers run on dedicated hardware without interference from other customer workloads.
Since Hathora provisions dedicated hardware per team, your container's traffic will be unaffected by noisy neighbor CPU and network traffic.
Hathora provisions compute across multiple cloud providers (AWS, GCP, Azure) and certified bare metal providers (i3D, Servers.com). Within cloud platforms, Hathora enforces isolation at the account and project level, ensuring each team operates within its own secure namespace.
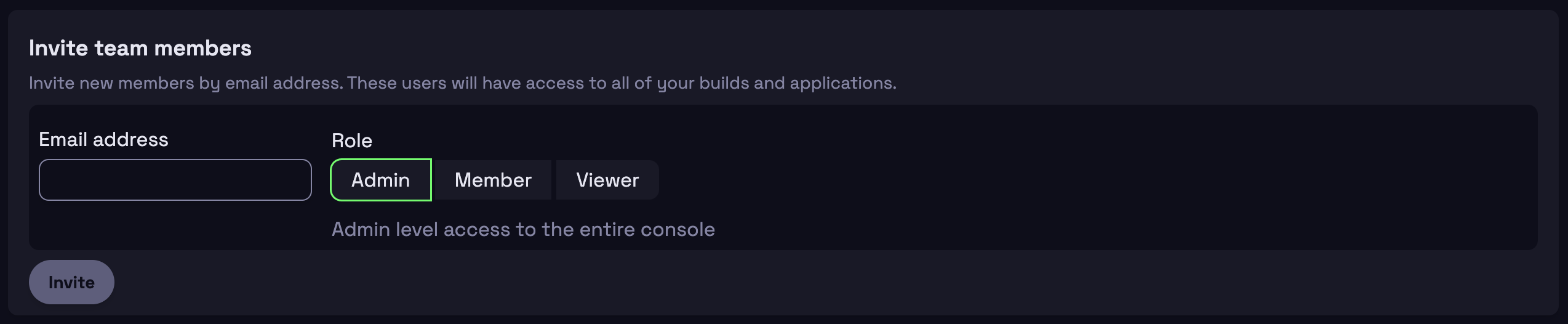
Workspace access control
Hathora supports account creation via Google Sign-In or email and password authentication for secure and seamless access.
Role-based access control (RBAC)
From the Team Dashboard, admins can configure least-privilege access for their employees, ensuring users have only the permissions they need. Learn more about scoped users.
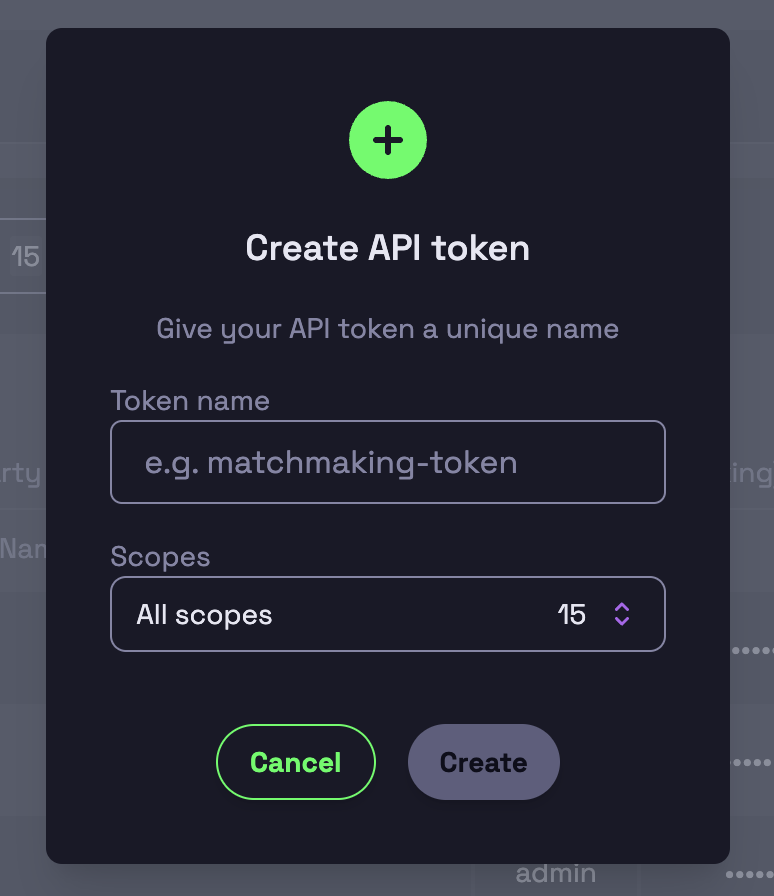
Scoped tokens
Hathora services use token-based authentication, allowing fine-grained access control:
- Scoped Tokens – Restrict tokens to specific permissions.
- Revocable Tokens – Admins can revoke tokens at any time to maintain security. Learn more about scoped tokens.
DDoS protection
DDoS protection at Hathora is built on the principle of defense in depth. We employ a combination of technologies across multiple layers of the stack: infrastructure, system, and application. Each are designed to mitigate different attack vectors.
Hathora defends against DDoS attacks using a comprehensive multi-tier strategy: defense in depth. Hathora employs a combination of technologies across multiple layers of the stack: infrastructure, system, and application. This layered approach effectively counters various DDoS attack vectors.
Basic DDoS protection
Every machine in the Hathora network has built-in protection against common DDoS attack vectors, including:
- UDP/ICMP/SYN floods – Overwhelming a server with packets to exhaust resources.
- Reflection attacks – Spoofing requests to amplify attack traffic.
- Amplification attacks – Exploiting open services to magnify traffic.
- Malformed packets – Filtering out corrupted or malicious packet structures.
- Traffic from known botnets and malicious networks – Blocking IPs flagged as threats.
Reputation-based blocklist
Hathora takes an opinionated approach to traffic management, ensuring only legitimate users reach your servers. Our reputation-based blocklisting pulls from multiple sources to block traffic originating from known botnets and compromised networks, significantly reducing attack surfaces.
Advanced DDoS protection
Advanced protection is only available for Enterprise customers.
Hathora offers an additional layer of defense through whitelist-based filtering, which activates only during an active DDoS attack.
You can provide a list of trusted player IPs when creating a room. If a DDoS attack is detected, all non-trusted IPs get throttled to avoid disruption of service.
{
"deploymentId": "dep-6d4c6a71-2d75-4b42-94e1-f312f57f33c5",
"clientIPs": ["172.16.200.45", "192.168.50.100", "4.53.149.90", "10.0.5.23"],
"roomConfig": "{\"name\":\"my-room\"}",
"region": "Seattle"
}
Rate limiting on allowlisted IPs
To further mitigate risks, each allowlisted clientIp is subject to rate limiting. This prevents even trusted IPs from overwhelming the server with excessive requests. By enforcing rate limits, we help maintain server stability, ensuring that high traffic—whether intentional or unintentional—does not disrupt or degrade performance.
Secure container registry
Builds represent container artifacts and are stored in Hathora's private Docker registry. Builds are securely uploaded to a signed URL over an encrypted HTTPS connection. Builds are only downloaded when explicitly necessary: spinning up a new server or pulling an update.
Data privacy
Application logs are encrypted at rest and served over TLS. Authenticated dashboards provide metrics.